Broken authentication is theft of user credentials, session tokens, keys, etc.. to gain unauthorized privilege. It is a threat inherent in an online platform or an application thereby enabling the hacker to bypass the authentication.
Attackers try broken authentication manually and attack them by using password lists and automated tools. Based on the system targeted, this will lead to money laundering, identity theft, social security fraud, and sensitive information disclosure.
It is listed as the second most dangerous threat in OWASP’s top 10 vulnerabilities.
Some of the Broken Authentication are listed down
- Phishing attacks
- Session ID URL
- Session Hijacking
- Password spraying
- Credential Stuffing
Phishing Attacks: Phishing starts with communication that is legitimately designed to coax the victim to provide information on a fraudulent page. The obtained information is generally used as part of financial gain or in some cases, it may even be used to launch advanced attacks on the organization.
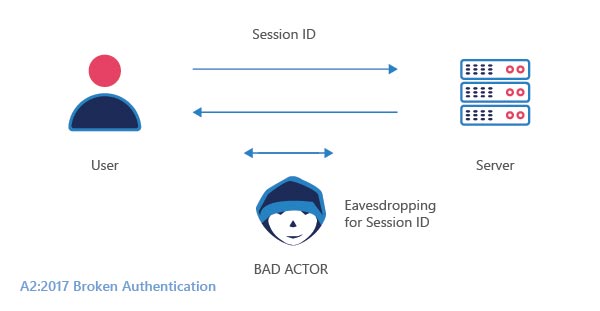
Session ID URL: Whenever a new session is created, the webserver creates a cookie and session id on the URL. This is done since the webserver is not sure whether the incoming client accepts cookies or not. Hackers make use of this phenomenon, and try to access the URL to take over the identity of the user.
Session Hijacking: Session hijacking is the process of taking over an active internet session. The hacker takes over an active session by predicting or stealing the valid session token to gain unauthorized access. Session hijacks are usually performed on busy networks which provides the attacker with a large number of sessions to exploit.
Password Spraying: Password spraying primarily targets accounts with commonly used passwords. The attackers generally use one password or use a list of commonly used passwords such as 123456789 to match the domain’s complexity.
The list of common target services are given below
- SSH
- Telnet
- FTP
- NetBIOS / SMB / Samba
- LDAP
- Kerberos
- RDP / Terminal Services
- HTTP/HTTP Management Services
- MSSQL
Credential Stuffing: Credential stuffing is the process of getting access to the login credentials of the user thereby leading to unauthorized access. This occurs mostly due to the data breaches where the organizations fail to maintain a dedicated password manager.
There are specific tools that use the combo list to crack the login credentials which enables the user to gain access.
How to mitigate these types of attacks?
- Multi-Factor Authentication
- Regulation of Session Length
- Web Application Firewall
Multi-Factor Authentication: Multi-Factor Authentication is when a user must undergo additional validation procedures to obtain access to an application or website. Since the chances of breaking into another factor are low, providing the user with multi-factor authentication will increase the security levels.
Session Length Regulation: The web applications must make sure that the session ends after a certain period of inactivity. This cramps the time of the hacker making it extremely difficult to breach into it.
WAF – Web Application Firewall
SQL injection attacks can be prevented with the help of a web application firewall (WAF). A WAF serves as a filter between the server and the web traffic.
A WAF works based on a set of rulesets, the most common type of ruleset used across any WAF is OWASP Top 10 ModSecurity rulesets. StrrongBox IT’s Modshield SB works on the core ModSecurity rulesets, which can avert SQL injections during the time of the attack.
Modshield SB – Get a 14-day free trial





