Amazon Web Services (AWS) offers a product called CloudFront, which, when combined with AWS WAF, helps businesses protect their web applications from intrusion. However, during an engagement, it was discovered that the “SQL Database” payload could be bypassed.

Why Modshield SB is a great AWS WAF alternate?
When Modshield SB(Our very own Web Application Firewall) encounters, the same payload is blocked by sensing the vulnerability and returns a 403 error message.
Payload:
Normal SQL Injection Payload:
Using the ‘id’ “value” as ‘ or 1 =1 — – => Brings the same content on the vulnerable page
Without firewall:
| GET /vulnerabilities/sqli/?id=%27%20or%20%27%27%20=%20%27%20–%20-&Submit=Submit HTTP/1.1 |
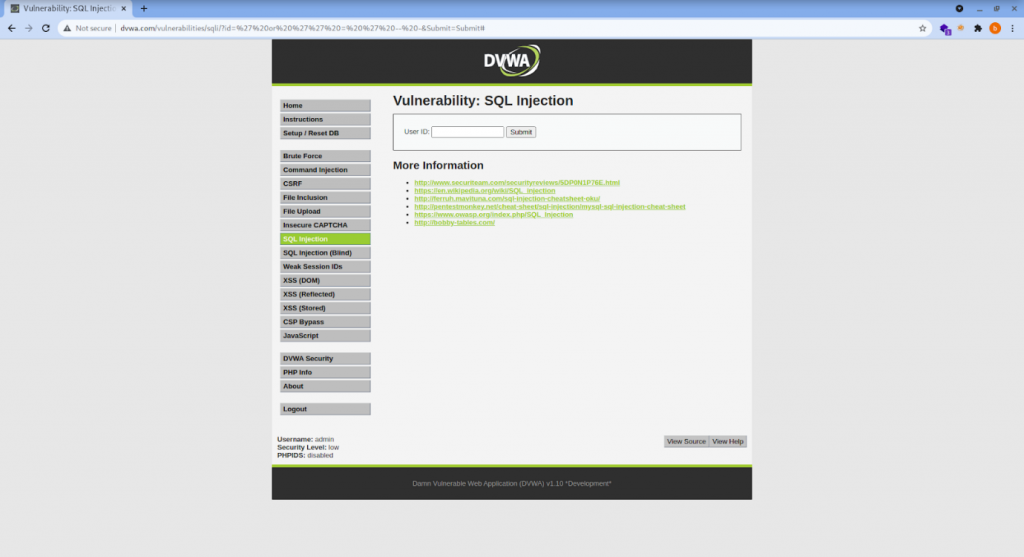
Without the protection of the firewall, the SQL payload executes successfully and renders the page as it is.
With MODSHIELD SB:
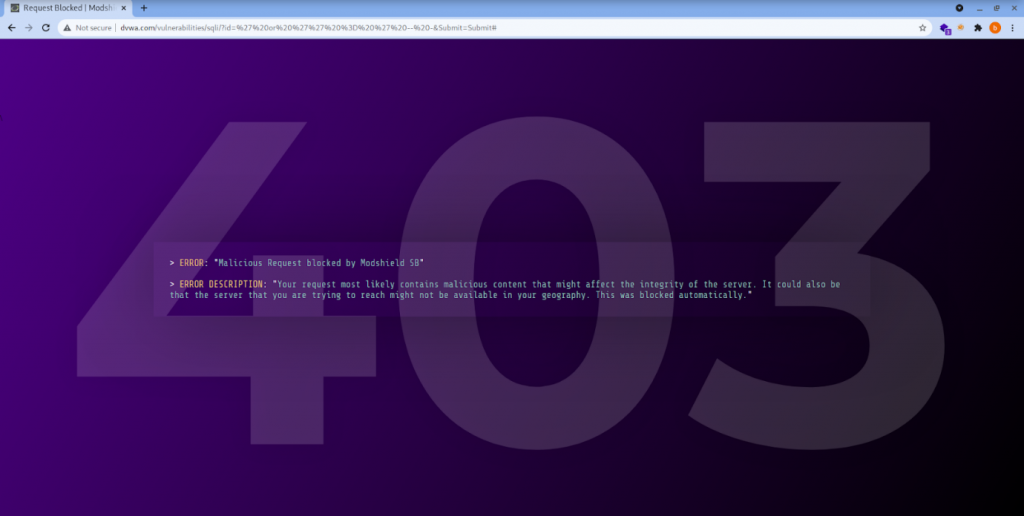
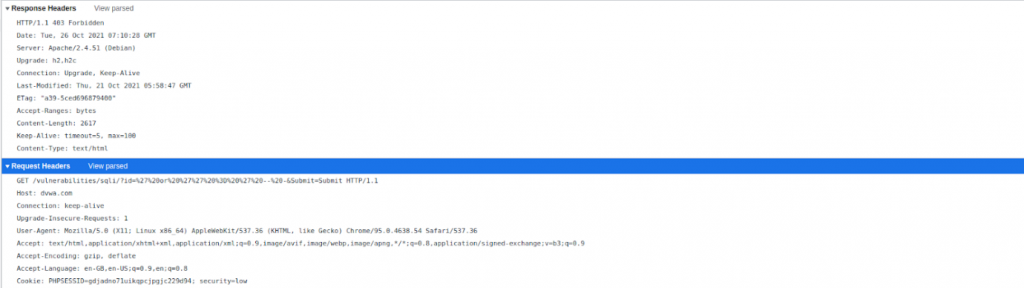
Scientific Notation Payload:
‘ or 1.e(”)=’ — – => processed successfully and brings the contents of the page as it is
Without firewall:
| GET /vulnerabilities/sqli/?id=%27%20or%201.e(%27%27)%3D%27%20–%20-&Submit=Submit HTTP/1.1 |
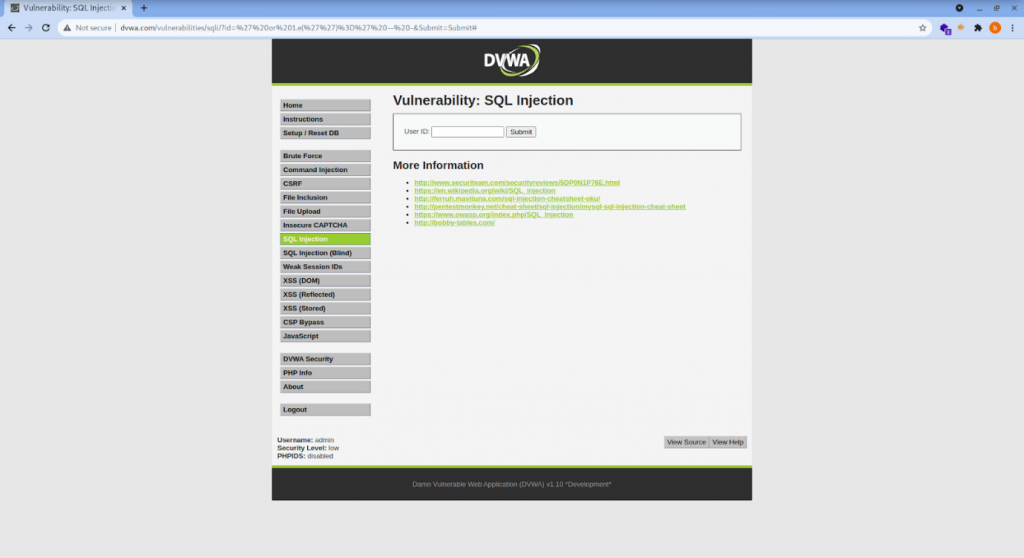
With firewall:
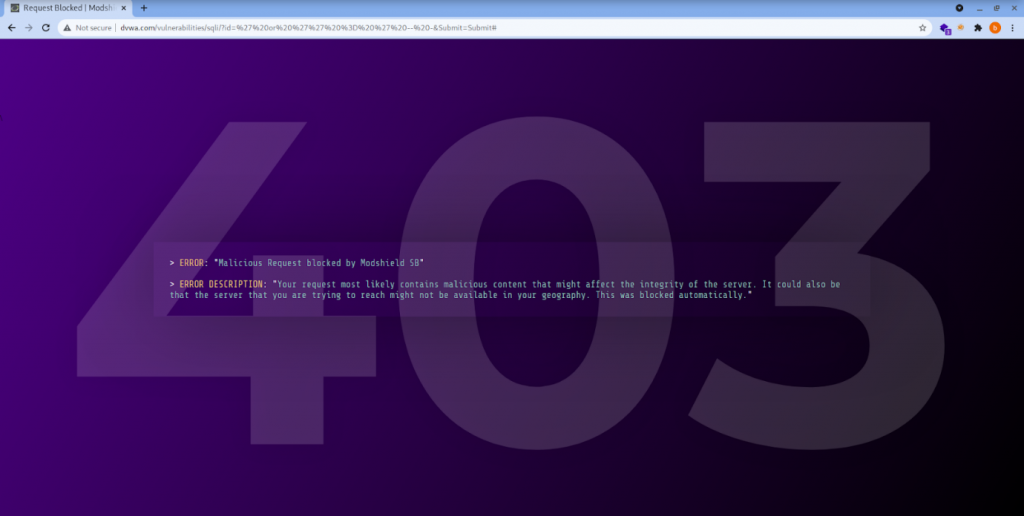
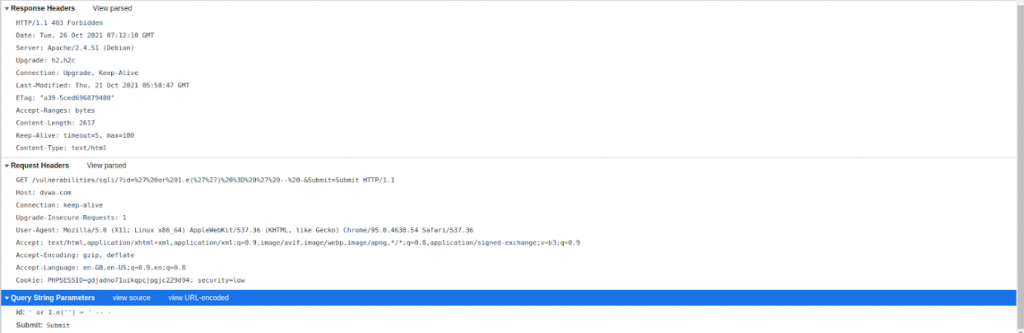
From the above elucidations, we can find that Modshield SB defends the payload whereas the AWS WAF fails to do so.
MODSHIELD SB WAF also defends against a wide range of web-based instructions and attacks that target applications hosted on the cloud and web applications. Modshield SB scans both inbound and outbound traffic, thereby protecting the user from attacks and preventing data loss (DLP). In addition, MODSHIELD SB protects from cross-site scripting (XSS), Server-side request forgery (SSRF), Sensitive data exposure, and other malicious attacks by hackers that compromise the privacy and integrity of sensitive data.





