WordPress is a secure platform for running your website as long as website owners adhere to best security practices. While the WordPress core is safe, there is still much that can be done to keep the website secure from threats.
Given the popularity of WordPress, there is a lot more to be gained by WordPress website attacks. Hackers actively invest time and effort in finding WordPress vulnerabilities so that they can replicate their efforts and attack millions of websites.
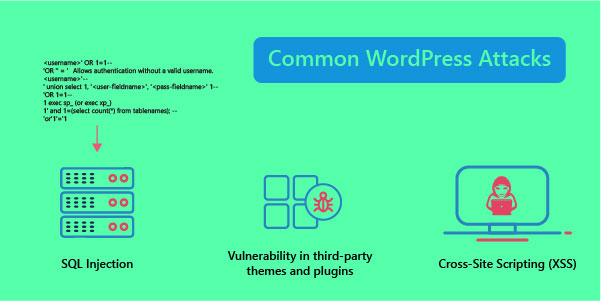
Common WordPress Attacks
Even though websites are highly secured, there is a tiny possibility that they still might be exposed to some major security attacks. By understanding the common attacks conducted on these websites, one can make their website safer.
Common WordPress attacks are listed below
- Cross-Site Scripting (XSS)
- SQL Injection
- Vulnerability in third-party themes and plugins
Cross-Site Scripting
Cross-Site Scripting (XSS) flaw occurs whenever the attacker makes use of DOM and API to retrieve data or send commands to the application.
Cross-site Scripting may widen the surface of the attack for the hacker by allowing him to hack user credentials, spread worms, and control browsers remotely.
An attacker tricks the web application to send data to an entity where the user’s browser can execute it. Cross-Site Scripting does not directly target the application but targets the users who are using it. If the user has access to confidential data, the attacker may take control over the entire application.
SQL Injection
An injection is a broad class of attack vectors. This flaw allows the malefactors to execute a discrete code on the host operating system through a vulnerable application. The attacker provides an altered input to a program. As this input gets executed as a part of a command or a query, the result gets altered. It could lead to data loss, data corruption, and loss of credibility.
Vulnerability In Third-Party Themes and Plugins
Usage of third-party software components in the development process may make your system vulnerable to attacks. Third-party application frameworks, libraries, technologies may have exposure to vulnerabilities. Using outdated components in nested dependencies, client-side and server-side failing to check the compatibility of updated library patches, may help the threat vectors to breach the system.
Install a WAF to secure your WP Website
Modshield SB WAF defends against a wide range of web-based instructions and attacks that target applications hosted on the cloud and web applications. Modshield SB scans both inbound and outbound traffic, thereby protecting the user from a wide array of cyber attacks and preventing data loss (DLP).
In addition, MODSHIELD SB protects from cross-site Scripting (XSS), Server-side request forgery (SSRF), Sensitive data exposure, and other malicious attacks by hackers that compromise the privacy and integrity of sensitive data. With the help of Modshield SB, one can protect their WordPress-based website with these simple steps.
How to Enable Modshield SB for WordPress
STEP 1: Open your MODSHIELD SB application and then click on configuration.
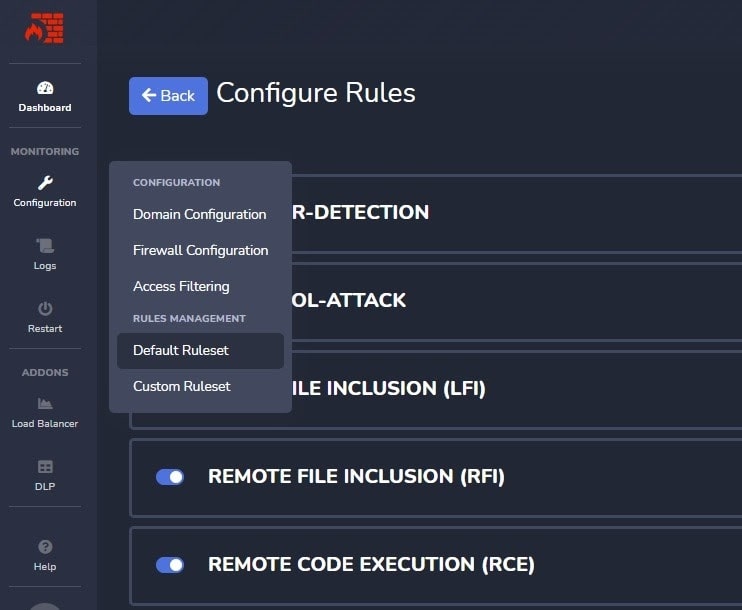
STEP 2: Configuration list box appears. On the configuration, the list box clicks on the default ruleset. You will be redirected to the Default Ruleset page.
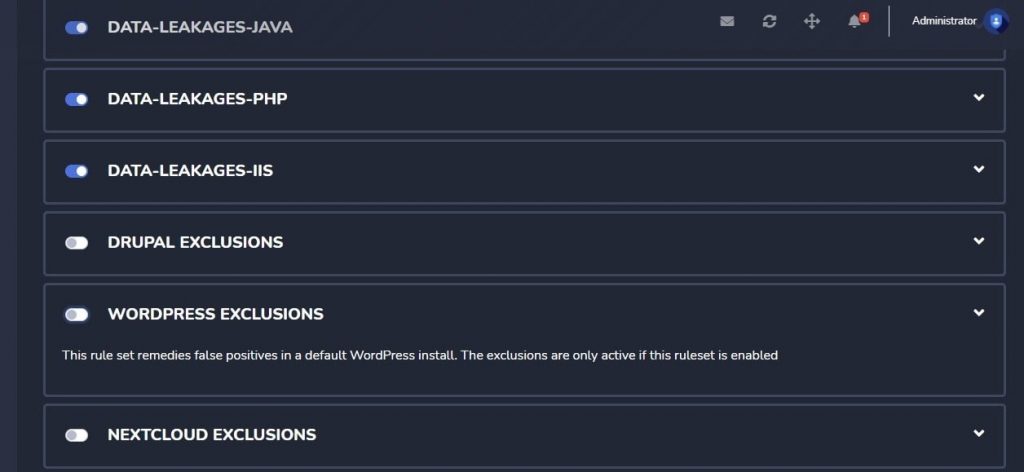
STEP 3: Enable the WORDPRESS exclusions tab. Once you have enabled it, your WordPress page is secured.
Try Modshield SB 30 day free trial





