Sensitive data is important information or an asset that needs to be protected. It includes personally identifiable information (PII), banking information, login credentials, etc.
Sensitive data exposure is the exposure of private data carelessly thereby leading to a breach in the entire system. The data being obtained is being sold or modified to conduct fraudulent activities.
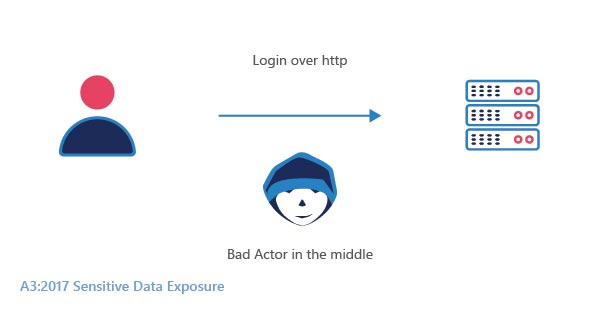
Data exposure occurs when the data is unencrypted in the database or server and can be easily accessed by everyone. It is the consequence of inadequate protection of the database.
Some of the attacks that expose sensitive data are as follows
- SQL Injection Attacks
- Ransomware Attacks
- Phishing Attacks
- Broken Access control attacks
- Disgruntled Employee Attacks
SQL Injection Attacks: An injection is a broad class of attack vectors where the attacker provides an altered input to a program. When the input gets executed as a part of a command or a query, the result obtained is completely altered. It is listed as the most dangerous threat in OWASP‘s top 10 vulnerabilities. This flaw allows the malefactors to execute a discrete code on the host operating system through a vulnerable application which leads to data loss, data corruption, and loss of credibility.
Phishing Attacks: Phishing starts with communication that is legitimately designed to coax the victim to provide information on a fraudulent page. The obtained information is generally used as part of financial gain or in some cases, it may even be used to launch advanced attacks on the organization.
Ransomware Attacks: These types of cyberattacks are carried out on the account of monetary benefits. They get hold of the company’s sensitive data or assets by breaching their security system in exchange for ransom.
Broken Access Control Attacks: The failure of the system to validate the user even after the user authentication is called Broken Access Control. This allows the user to bypass the basic access controls without proper validation. This leads to admin-level data exposure which in turn may lead to several other complications.
Disgruntled Employees Attacks: Ex-Employees who had a bad past in an organization or employees who are dissatisfied with their roles are prone to tampering with the system. They could retain certain access to the company’s systems and may pose a serious vulnerability by sabotaging cyber security measures or may leak the company’s assets as a means of showing their recrimination.
PREVENTION FROM SENSITIVE DATA EXPOSURE:
- Data Encryption
- Web Application Firewall
Data Encryption: Data encryption is the method of converting the data into encoded information. The encrypted data can only be with the help of a decrypted key that is generated beforehand or at the time of encryption.
Web Application Firewall: Web Applications Firewalls with custom rules sets and targeted policies will help in preventing sensitive data exposure. A WAF serves as a filter between the server and the web traffic.
A WAF works based on a set of rulesets, the most common type of ruleset used across any WAF is OWASP Top 10 ModSecurity rulesets. StrongBox IT’s Modshield SB works on the core ModSecurity rulesets, which can avert SQL injections during the time of the attack.





