Cyber threats are becoming more sophisticated and persistent, safeguarding sensitive data is paramount for businesses. From ransomware attacks to data breaches, organizations face constant threats that can compromise their operations and reputation. A network security audit serves as a critical safeguard, enabling businesses to identify vulnerabilities, strengthen defenses, and ensure data protection. This blog delves into the concept of a network security audit, its key components, and how it helps maintain data safety.
What is a Network Security Audit?
A network security audit is a systematic evaluation of an organization’s IT infrastructure to identify vulnerabilities, risks, and compliance gaps. It involves assessing the effectiveness of existing security measures, ensuring adherence to industry standards, and providing actionable recommendations to improve the overall security posture. The primary goal of a network security audit is to minimize risks, protect sensitive information, and maintain business continuity.
Key Components of a Network Security Audit
Why is a Network Security Audit Important?
A network security audit is crucial for identifying vulnerabilities and gaps in an organization’s IT infrastructure, ensuring a robust defense against potential cyber threats. In today’s interconnected world, networks serve as the backbone of business operations, making them prime targets for cyberattacks. An audit assesses the security controls, configurations, and policies to identify risks such as unauthorized access, outdated software, or weak passwords. By doing so, organizations can proactively mitigate these risks, prevent data breaches, and protect sensitive information, ensuring compliance with regulatory standards like GDPR, HIPAA, or ISO 27001. This helps maintain customer trust and safeguards the organization’s reputation.
Beyond risk mitigation, a network security audit plays a vital role in optimizing system performance and aligning security strategies with business goals. It provides valuable insights into network activity, helping to detect inefficiencies, bottlenecks, or unusual traffic that could indicate malware or unauthorized activities. Additionally, the audit fosters a culture of continuous improvement by identifying areas for upgrading security protocols and adopting emerging technologies.
Key Steps in Conducting a Network Security Audit
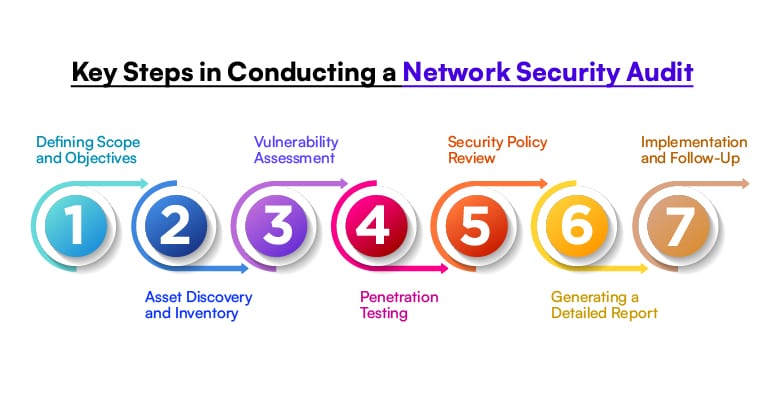
1. Defining Scope and Objectives:
Begin by establishing the goals and scope of the audit. This includes identifying which networks, systems, and assets will be assessed, as well as the compliance requirements or security frameworks to follow. Clear objectives ensure the audit is focused and aligned with business priorities.
2. Asset Discovery and Inventory:
Conduct a thorough inventory of all network devices, systems, and software. This step identifies critical assets, including servers, routers, endpoints, and cloud resources, along with their associated data flows. It ensures no component of the network is overlooked during the audit.
3. Vulnerability Assessment:
Use automated tools and manual methods to evaluate the network for vulnerabilities, such as unpatched software, misconfigurations, or weak access controls. This step helps in prioritizing risks based on their severity and potential impact.
4. Penetration Testing:
Simulate cyberattacks on the network to assess its resilience against real-world threats. Penetration testing provides insights into exploitable vulnerabilities and helps validate the effectiveness of existing security controls.
5. Security Policy Review:
Examine the organization’s security policies and procedures to ensure they are up to date and effectively implemented. This includes reviewing access controls, incident response plans, and data protection measures to ensure compliance with industry standards.
6. Generating a Detailed Report:
Document the findings in a comprehensive report. This report should include identified vulnerabilities, their potential impact, and actionable recommendations for remediation. A clear, detailed report serves as a roadmap for improving network security.
7. Implementation and Follow-Up:
Implement the recommended measures to address identified issues, such as patching vulnerabilities or updating security policies. Conduct follow-up audits to verify that changes have been effective and to ensure continuous network security improvement.
Common Vulnerabilities Identified in Network Security Audits
- Outdated or weak encryption protocols.
- Unpatched software vulnerabilities.
- Misconfigured firewalls or routers.
- Insufficient access controls and privilege management.
- Lack of regular backups and disaster recovery plans.
- Inadequate monitoring and logging mechanisms.
Benefits of a Network Security Audit
Why Choose Professional Network Security Audit Services?
1. Expertise: Access to certified professionals with in-depth knowledge of cybersecurity practices.
2. Advanced Tools: Utilization of cutting-edge technologies for thorough assessments.
3. Objective Assessment: Unbiased identification of vulnerabilities and risks.
4. Customized Solutions: Tailored recommendations based on your organization’s unique needs.
5. Time Efficiency: Professionals can conduct audits more efficiently, minimizing disruptions to business operations.
StrongBox IT: Your Trusted Partner in Network Security Audits
At StrongBox IT, we specialize in delivering comprehensive network security audits that safeguard your organization’s data and operations. Our team of certified experts uses state-of-the-art tools and methodologies to:
- Identify and address vulnerabilities.
- Ensure compliance with regulatory standards.
- Provide actionable insights to enhance your security posture.
With years of experience in the cybersecurity domain, we are committed to helping businesses achieve robust network security. Protect your business with StrongBox IT’s trusted network security audit services.
Contact us today to secure your network and ensure your data stays safe!





