IEC 62443 is an international series of standards that address automation and control systems cybersecurity. The standard is organized into sections that address cybersecurity’s technical and process elements in automation and control systems.

In addition, it categorizes cybersecurity topics based on stakeholder categories/roles, such as the operator, service providers (integration and maintenance), and component/system manufacturers. The various roles each take a risk-based approach to prevent and manage security risks in their activities.
IEC 62443 specifies various levels of maturity for processes and technical requirements. The maturity levels for operations are based on the CMMI framework’s maturity levels.
IEC 62443 Maturity Degree
IEC 62443, based on CMMI, describes different maturity levels for processes through so-called “maturity levels.” To achieve a certain level of maturity, all process-related requirements must be followed at all times during product development or integration; choosing only individual criteria (“cherry-picking”) is not standard-compliant.
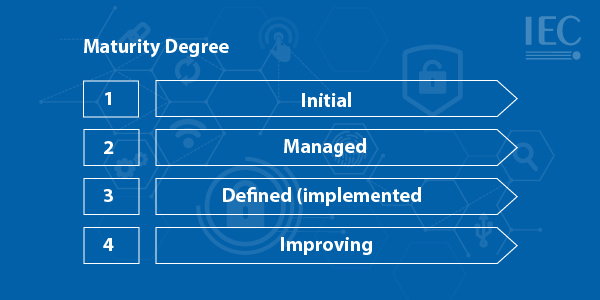
The levels of maturity are as follows:
Maturity Level 1 – Initial
Product vendors often carry out ad hoc and undocumented product development.
Maturity Level 2 – Managed
The product supplier can manage product development following written guidelines. It must be demonstrated that the personnel performing the process have the necessary expertise, are trained, and adhere to written procedures. The procedures can be repeated.
Maturity Level 3 – Defined (implemented)
The process is repeatable across the supplier’s organization. The procedures have been carried out, and there is evidence that this has occurred.
Maturity Level 4 – Improving
Product suppliers use appropriate process metrics to monitor the effectiveness and performance of the process and demonstrate continuous improvement in these areas.
Security degree
The standard evaluates technical requirements for systems (IEC 62443-3-3) and products (IEC 62443-4-2) using four so-called Security Levels (SL). The different levels represent resistance to varying types of attackers. However, the standard emphasizes that the levels should be evaluated according to technical requirements (see IEC 62443-1-1) and are not suitable for general product classification.
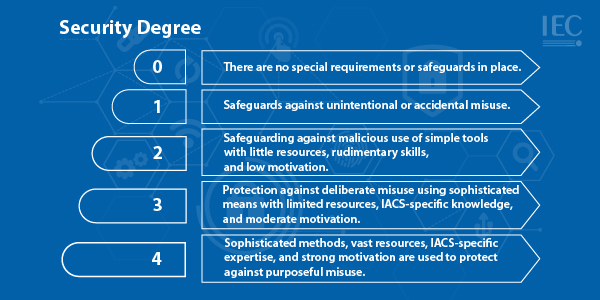
The levels are as follows:
Level 0 security
There are no special requirements or safeguards in place.
Level 1 security
Safeguards against unintentional or accidental misuse.
Level 2 security
safeguarding against malicious use of simple tools with little resources, rudimentary skills, and low motivation.
Level 3 security
Protection against deliberate misuse using sophisticated means with limited resources, IACS-specific knowledge, and moderate motivation.
Level 4 security
Sophisticated methods, vast resources, IACS-specific expertise, and strong motivation are used to protect against purposeful misuse.





